Network Detection & Response
See Everything. Stop Anything.
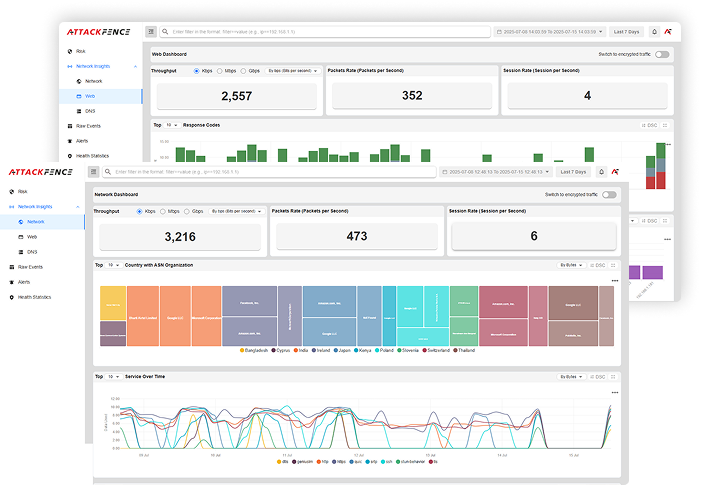
Why AttackFence NDR?
Complete network visibility meets intelligent threat detection

Comprehensive Visibility
- 100% network traffic analysis without sampling
- Full packet capture and forensics capability
- Passive monitoring with zero performance impact
- See north-south and east-west traffic
- Real-time flow analysis and visualization
- Deep packet inspection capabilities
- Historical data retention for forensics
Advanced Threat Detection
- ML-based detection for zero-day threats
- MITRE ATT&CK™ framework mapping
- Entropy-based encrypted traffic analysis
- Real-time threat intelligence correlation
- Behavioral anomaly detection
- Custom detection rule creation
- Threat actor profiling
Rapid Response
- Automated alert prioritization
- Integrated response orchestration
- Forensic evidence preservation
- Seamless SIEM/SOAR integration
- One-click threat containment
- Automated playbook execution
- Real-time stakeholder notification
Technical Capabilities
Scalable performance and comprehensive protocol support
Network Layer Support
- IPv4/IPv6: Complete dual-stack support
- TCP/UDP: Full session reconstruction
- ICMP/ICMPv6: Network diagnostics monitoring
- GRE/IPSEC/MPLS: Tunnel and VPN support
- VLAN/VXLAN: Virtual network visibility
- 802.1Q: VLAN tagging support
- Jumbo frames: Up to 9000 MTU

Application Layer Analysis
- Web: HTTP/HTTPS with SSL/TLS inspection
- Email: SMTP, POP3, IMAP monitoring
- File Transfer: FTP, SMB/CIFS
- Database: MS SQL, MySQL, PostgreSQL
- VoIP: SIP, RTP, H.323 protocols
- DNS: Query analysis and DGA detection
- Custom protocols: Parser SDK available

Flow Ingestion
- IPFIX (IETF RFC7011) - latest standard
- NetFlow v5, v9, and Flexible NetFlow
- sFlow v5 for sampled monitoring
- J-Flow (Juniper)
- NetStream (Huawei)
- AppFlow (Citrix)
- Custom flow formats supported

Hardware Specifications
- Standard: 4x1 GbE monitoring ports per device
- High-Performance: 2x1/10Gb SFP monitoring ports
- Ultra: 2x40 Gb QSFP+monitoring ports
- Throughput: Up to 40 Gbps or 200,000 flows/second
- Redundancy: Active-Standby configuration support
- Storage: 8TB to 96TB options available
- Form Factor: 1U/2U rack-mountable appliances

Multi-Layered Detection Engine
Stacked detection methods for comprehensive threat coverage

NDR Use Case Scenarios
Real-world attack detection and response examples
Integration Ecosystem
Seamlessly integrates with your existing security stack
SIEM Integration
Enrich your SIEM with high-fidelity network data
Supported Platforms:
- Splunk Enterprise & Cloud
- IBM QRadar
- Micro Focus ArcSight
- LogRhythm NextGen
- Elastic Security
- Custom integration via REST API
SOAR Platforms
Automate response with playbook integration
Supported Platforms:
- Splunk Phantom/SOAR
- Palo Alto Cortex XSOAR
- IBM Resilient
- ServiceNow Security Operations
- Rapid7 InsightConnect
- Custom playbook support
Network Security
Coordinate defense with network security tools
Supported Integrations:
- Palo Alto Networks
- Fortinet FortiGate
- Check Point
- Cisco ASA/Firepower
- F5 BIG-IP
- SD-WAN controllers
Deployment Options
Flexible deployment models to match your infrastructure
On-Premises Deployment
Perfect for: Organizations requiring data sovereigntyBenefits:
- Complete data control and privacy
- Air-gapped security option available
- Meet strict compliance requirements
- No external cloud dependencies
- Dedicated hardware performance
Requirements:
- Physical/virtual appliance deployment
- Network TAP or SPAN port access
- Storage infrastructure (NAS/SAN)
- Management network connectivity
Cloud Deployment
Perfect for: Cloud-first organizationsBenefits:
- Infinite scalability on demand
- No hardware management overhead
- Global deployment in minutes
- Pay-as-you-grow pricing model
- Built-in high availability
Supported Platforms:
- AWS with VPC Traffic Mirroring
- Azure with Virtual Network TAP
- Google Cloud Packet Mirroring
- Multi-cloud deployments supported
Hybrid Deployment
Perfect for: Distributed enterprisesBenefits:
- Infinite scalability on demand
- No hardware management overhead
- Global deployment in minutes
- Pay-as-you-grow pricing model
- Built-in high availability
Supported Platforms:
- AWS with VPC Traffic Mirroring
- Azure with Virtual Network TAP
- Google Cloud Packet Mirroring
- Multi-cloud deployments supported

